Best Practices for Agent-to-Agent Authentication
Oct 7, 2025
5
Matt (Co-Founder and CEO)
Agent-to-agent authentication is a security method that ensures AI agents interact securely by verifying their identities through unique credentials like service accounts, certificates, or tokens. This approach eliminates shared credentials and reduces risks, especially as agents handle tasks autonomously across systems like CRMs and APIs.
Key takeaways:
Zero Trust: Always verify credentials for every request.
Least Privilege: Limit agent access to only what’s necessary.
Continuous Verification: Use short-lived credentials and monitor behavior for anomalies.
Steps for implementation:
Assign unique identities to each agent (e.g., client IDs or certificates).
Use secure methods like OAuth client credentials flow and mutual TLS (mTLS).
Automate token management and rotation for scalability.
Monitor and log all agent activities to maintain compliance and accountability.
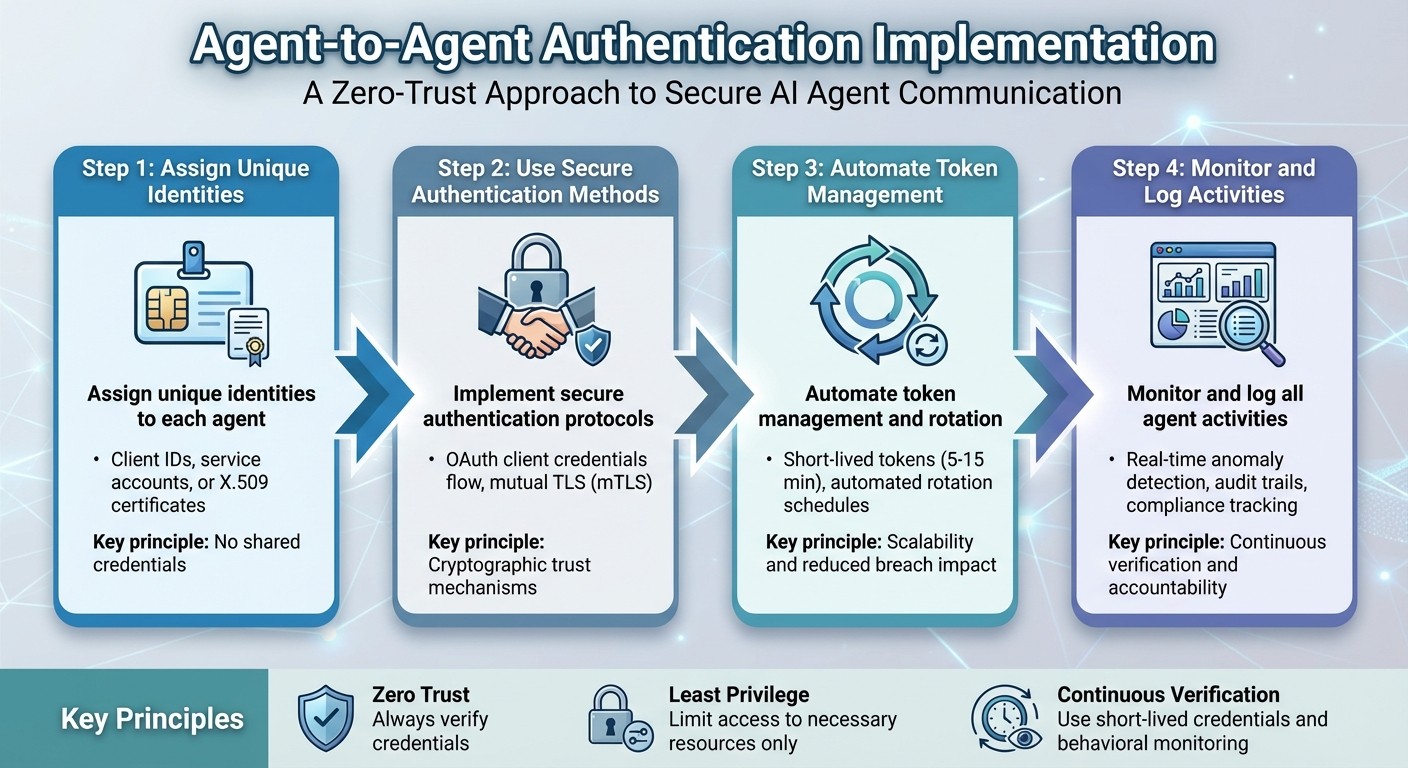
{4-Step Implementation Process for Agent-to-Agent Authentication}
Securing AI Agents (A2A and MCP) with OAuth2 – Human and Agent Authentication for the Enterprise
Building Secure Agent Identities
Every AI agent needs its own identity linked directly to its actions. Sharing credentials not only increases the risk of breaches but also makes it nearly impossible for forensic teams to trace specific actions back to the responsible agent. For instance, if two agents share a CRM service account, compromising one agent jeopardizes both and creates a major security blind spot.
Creating Unique Agent Identities
Each agent should have its own dedicated service account, client ID, or X.509 certificate tailored to its specific role. Imagine one agent handling CRM data while another manages billing adjustments - these two should never share credentials. According to ISACA, shared service accounts expand the potential damage during a breach and make audit trails difficult to interpret. If an attacker gains access to one agent, they could impersonate others and access systems far beyond the original compromise.
For environments requiring higher security, hardware-bound keys stored in HSMs (Hardware Security Modules) or TPMs (Trusted Platform Modules) are a safer choice. These keys remain tied to specific hardware and can’t be extracted, even if the agent’s software is compromised. This approach aligns with zero-trust principles, ensuring credentials can’t be reused in unauthorized ways.
Managing Agent Identity Lifecycles
Agent identities are not static; they go through phases, including creation, registration, updates, and deactivation. Start by provisioning agents through a standardized workflow: register them in the IAM system, assign ownership, and issue short-lived credentials. If an agent’s role changes - like a support agent gaining access to a new data lake - issue a new token with updated permissions instead of expanding existing ones. This prevents authorization creep, where agents accumulate excessive, unintended privileges over time.
When an agent is retired or no longer in use, revoke its tokens, rotate keys, and disable its identity immediately. Orphaned credentials are a known vulnerability in large-scale deployments, especially when agents are ephemeral and frequently created or destroyed. Ping Identity suggests tracking agent versions in the IAM system to link each identity to a specific model or software release. This makes it easier to audit changes and respond to incidents effectively.
Using Cryptographic Trust Mechanisms
For secure agent-to-agent authentication, Mutual TLS (mTLS) is a top choice. During a TLS handshake, both the client and server present certificates verified against a trusted Certificate Authority (CA). This ensures both parties are authentic, effectively blocking man-in-the-middle attacks. Red Hat’s Agent2Agent (A2A) protocol guidance highlights the importance of validating peer certificates against fields like subject or subjectAltName (e.g., agent names or DNS entries) and checking revocation lists or OCSP responses to detect compromised certificates.
JWT tokens work well alongside mTLS by embedding agent claims - such as client ID, roles, scopes, and environment - into a signed payload. The receiving agent verifies the token’s signature without relying on a shared secret, enabling stateless authentication across multiple steps in a workflow. To enhance security, use short token lifetimes (just a few minutes), bind tokens to specific clients through mechanisms like Demonstrable Proof of Possession (DPoP) or mTLS, and rotate keys frequently to minimize the impact if a token is stolen. By combining mTLS and JWTs, you create a layered defense that ensures every interaction is both authenticated and traceable. These measures set the stage for more advanced authentication strategies discussed in later sections.
Authentication Methods for Agent Communication
Once you've assigned unique identities to your agents, the next step is selecting the right authentication methods. The aim here is to confirm that each agent is exactly who it claims to be before it communicates with other agents or services. In enterprise settings, three common approaches often surface: OAuth client credentials, mutual TLS (mTLS), and delegation frameworks for multi-hop workflows. For added security, organizations often combine these methods. Let’s take a closer look at how these techniques secure inter-agent communication.
OAuth Client Credentials Flow
When an agent needs to access an API or service as itself - rather than on behalf of a user - the OAuth 2.0 client credentials flow is a go-to solution. In this setup, the agent registers as a confidential client with a unique client ID and a secret (or certificate). It then uses these credentials to obtain a short-lived JWT (JSON Web Token) that includes its identity, roles, and permissions.
To limit the risk of token misuse in case of compromise, it's best to rotate tokens every 15–60 minutes. Centralized token introspection and revocation are key here - they allow you to immediately revoke access if an agent is compromised. Additionally, integrating with SIEM systems can help detect unusual request patterns, giving you an early warning of potential issues.
mTLS for Peer Authentication
For transport-level security, mutual TLS (mTLS) is a powerful option. This method requires both the client and server to present valid certificates during the TLS handshake, ensuring strong cryptographic proof of identity before any data is exchanged. Unlike token-based methods, mTLS doesn’t rely on shared secrets between agents, making it even more secure.
To strengthen mTLS, automate certificate issuance, rotation, and revocation using internal PKI systems or service meshes. Sidecar proxies can also simplify the process by injecting certificates into outbound calls, so agents don’t have to manage long-lived secrets. Make sure to enforce modern TLS versions and secure cipher suites to guard against downgrade attacks. In high-traffic environments, enabling TLS session resumption can reduce handshake overhead without compromising security.
Delegation and Multi-Hop Authentication
For workflows where agents act on behalf of users, delegation and multi-hop authentication methods provide accountability. In these cases, agents receive scoped, time-limited tokens. Instead of passing the same token between hops, issue a new, restricted token at each step. These tokens should include audience restrictions and short expiration times.
This strategy helps prevent "confused deputy" attacks, where an agent might misuse elevated privileges. To ensure proper validation, tokens or headers should include both the acting agent’s identity and the original user’s identity. For highly sensitive actions, consider adding human-in-the-loop approvals and log each step for auditing purposes. Techniques like DPoP (Demonstration of Proof-of-Possession) or mTLS can also bind tokens to specific clients, reducing the risk of unauthorized token use.
Scaling Authentication for Large Agent Networks
As your agent network expands from a few to hundreds - or even thousands - of agents, authentication processes can become a bottleneck. Centralized authorization servers may struggle to handle the surge in TLS handshakes and token issuance, putting zero-trust execution at risk. To address these challenges, it's crucial to focus on token management, performance optimization, and network segmentation. Here's how you can scale authentication effectively.
Token Management and Rotation
Short-lived access tokens (lasting 5–15 minutes) are a key strategy for minimizing the impact of security breaches at scale. These tokens work alongside longer-lived refresh tokens, which are carefully protected and rotated on a set schedule - often every few days or weeks. This approach ensures regular reauthentication while keeping the load on authorization servers manageable.
To further streamline operations:
Cache tokens based on audience, scope, and tenant, and refresh them shortly before they expire. Adding a safety margin prevents interruptions.
Use service meshes to centralize token management. By injecting tokens into outbound calls, agents are freed from handling credentials directly.
Credential rotation should be fully automated through policy-driven workflows. Techniques like blue/green or dual-key rotation - where old and new keys remain valid during a brief overlap - can help avoid downtime. Tools such as Prefactor simplify this process by orchestrating rotation schedules, maintaining audit trails, and ensuring no agent operates with expired credentials in production.
Performance Optimization Techniques
When authentication loads increase, performance optimization becomes critical. Here are some methods to handle high-throughput demands:
Connection pooling: Reuse existing TCP/TLS sessions to reduce overhead. For mTLS, segregate connection pools by identity and tenant to avoid credential mix-ups.
HTTP/2 or HTTP/3: These protocols support multiplexed streams, allowing multiple logical requests over a single connection, which reduces overhead.
Token reuse: Cache tokens and reuse them across multiple requests, provided the audience and scope align. This reduces the frequency of token requests.
Asynchronous patterns: For high-throughput operations, batch requests or use asynchronous workflows to reduce load. Agents can pass an authorization reference via queues or streams, allowing worker agents to fetch fresh, scoped tokens only when needed.
Rate limiting and backoff strategies at both agent and gateway levels help prevent sudden spikes in token requests from overwhelming the system. Ensure that asynchronous tokens have a limited time-to-live (TTL) and include traceable audit links for security.
Multi-Tenant and Environment Segmentation
For multi-tenant environments, strict boundaries are essential. Each tenant should have:
A distinct identity namespace.
Separate OAuth clients or audiences.
Unique key material or certificate hierarchies for mTLS.
Tokens must include tenant identifiers and be validated against tenant-specific policies. This prevents agents from one tenant from using tokens intended for another. Additionally, caches should be isolated per tenant and environment to avoid cross-contamination.
Environment segmentation - covering development, testing, staging, and production - requires a similar level of separation. Each environment should have:
Its own identity providers, credentials, and endpoints.
Separate OAuth clients, audiences, and signing keys.
Service accounts and agent IDs should be scoped by environment, with naming conventions that clearly indicate their origin. Automating the provisioning of environment-specific credentials through CI/CD pipelines ensures that test agents or ephemeral environments are properly decommissioned.
Authorization policies should adapt to both tenant and environmental parameters. For example, the same logical role might grant different rights depending on the tenant or environment. In cases where compliance requires strong isolation, consider separate deployment environments, network segmentation, or even dedicated clusters for each tenant. Centralized platforms like Prefactor can enforce per-tenant limits, provide operational visibility, and help establish consistent policy baselines for compliance teams.
Governance and Monitoring for Agent Authentication
In the context of agent authentication, governance and monitoring play a vital role in maintaining security across dynamic enterprise environments. While authentication acts as the initial checkpoint, governance and monitoring ensure ongoing compliance and accountability. This shifts authentication from a one-time process into a continuous system that tracks agent activities, detects anomalies in real time, and generates audit trails to meet regulations like SOC 2, GDPR, and other industry standards.
Security Logging and Audit Trails
Every action performed by an authenticated agent should create a detailed log. These logs should capture essential data, such as agent identity, delegated scope, accessed resource, timestamp, origin, and the outcome of the action. This level of detail ensures clear and traceable audit trails, which are crucial for quick investigations.
Logs should be structured in a standardized, queryable format - commonly JSON with consistent field names. Key elements include:
Agent identity
Authentication method (e.g., OAuth client credentials or mTLS)
Token or certificate identifiers
Scopes and roles
Resource identifiers
Action type (e.g., read, write, admin)
Decision (allow or deny)
Risk scores
Correlation IDs that link multi-step processes into a single trace
For SOC 2 compliance, logs must cover authentication events, access attempts, privilege changes, configuration updates, and security incidents. Retention periods typically range from one to seven years, depending on your organization’s policy. GDPR adds further requirements, such as data minimization - logging only identifiers and metadata rather than full content - and clear justification for storing personal data. Additionally, processes must be in place to honor access and deletion requests without compromising security evidence.
Logs should be stored in a secure platform or SIEM with encryption (both at rest and in transit using TLS 1.2+), strict role-based access controls, and tamper-proof mechanisms like append-only storage or cryptographic hashing. Implement dual-control for exporting or deleting logs, and isolate tenant or environment caches. Organizations serving EU residents but operating primarily in the U.S. must ensure logs are stored in U.S.-based data centers with documented data flows and appropriate safeguards for cross-border transfers.
Continuous Verification and Anomaly Detection
Authentication isn’t enough on its own - trust must be continuously reassessed. Continuous verification ensures that every action is evaluated in real time using short-lived credentials, context-aware permissions, and behavioral analytics. This approach monitors signals like:
Request rate and burst patterns
Resource access trends
Geographic or network changes
Deviations from established behavioral baselines
Unusual delegation chains
Attempts to access higher-privilege scopes than typically required
Start with simple rule-based systems, such as threshold alerts and deny-lists for prohibited resource combinations. Over time, move toward advanced statistical and machine-learning models that learn normal agent behavior and flag unusual activity. For example, if a customer support agent who typically processes 50 tickets per hour suddenly starts exporting all tickets or accessing financial APIs, the system should detect and act on this anomaly in real time.
Automate responses to anomalies. For minor risks, throttle activity or issue challenges. For critical threats, revoke tokens, quarantine the account, and alert security teams immediately. These processes can be integrated into SOAR platforms, enabling automated workflows. For instance, if an agent exceeds a set number of requests per minute to financial APIs from an unfamiliar region, the system could automatically block the activity, open an incident report, and attach the full activity trace for review.
Prefactor builds on these principles to deliver a comprehensive governance solution.
How Prefactor Enables Governance

Prefactor provides real-time visibility and detailed audit trails for every agent action. Each activity is logged with full context - tracking who did what, when, and why - making it easy for security teams to respond to audit requests in minutes instead of days. Prefactor’s policy-as-code approach ensures that authentication and authorization policies are version-controlled, testable, and integrated into CI/CD pipelines. This guarantees that access decisions are both transparent and aligned with organizational intent.
Conclusion
Secure agent-to-agent authentication hinges on unique agent identities - no shared service accounts or reused credentials. Every agent should have its own identity tied to a human custodian, ensuring clear audit trails and reducing the impact of potential breaches. Adopting zero-trust principles is key: continuously verify identities, use short-lived tokens, and enforce least-privilege access for every request. For transport security, rely on mTLS, and for authorization, implement OAuth client credentials or delegation flows to prevent agents from sharing user credentials or bypassing authentication protocols.
As agent networks grow, token management and rotation become increasingly important. Automate credential deployment with tools like service meshes or API gateways, adopt just-in-time (JIT) access, and segment environments to isolate tenants effectively. Additionally, using behavioral baselines and anomaly detection can help identify unusual agent activity - such as an agent suddenly flooding email APIs or accessing sensitive financial data it normally wouldn’t - before it escalates into a larger issue. These measures ensure continuous oversight and operational integrity.
Governance and monitoring elevate authentication into an ongoing, verifiable process. Every agent action should be logged with full context, policies enforced as code through CI/CD pipelines, and human approvals required for high-risk actions. According to ISACA, 95% of agentic AI projects fail due to accountability gaps. The difference between a proof-of-concept and a production-grade deployment lies in governance: knowing exactly who did what, when, and why.
To address these challenges, Prefactor provides the tools needed for comprehensive governance. It offers visibility, audit trails, and compliance controls that integrate seamlessly with existing OAuth/OIDC infrastructures. By centralizing policy enforcement and lifecycle management, Prefactor enables enterprises to scale AI agent deployment while maintaining the security, compliance, and control demanded by regulators and stakeholders. While authentication forms the foundation, governance is what transforms agent networks into production-ready systems.
FAQs
What role does mutual TLS play in securing agent-to-agent authentication?
Mutual TLS enhances security in agent-to-agent authentication by requiring both agents to verify each other's identities through cryptographic certificates. This ensures that communication happens only between agents with valid credentials, blocking impersonation attempts and man-in-the-middle attacks.
Through the exchange and validation of certificates, mutual TLS establishes a secure and trusted communication channel, offering strong protection for sensitive enterprise operations.
Why are short-lived tokens important for agent authentication?
Short-lived tokens play a key role in strengthening security during agent authentication. By restricting the window of time in which a token is valid, they reduce the chances of unauthorized access. Even if a token is compromised, the limited lifespan minimizes the potential harm.
These tokens also simplify processes in fast-changing environments. With their ability to renew automatically and frequently, they remove the need for manual updates. This keeps authentication secure and efficient, even in the most intricate enterprise systems.
Why is assigning unique identities to AI agents essential?
Assigning distinct identities to AI agents plays a key role in maintaining security, accountability, and effective management. By doing so, you can precisely monitor each agent's activities, verify their authenticity, and control their access to resources with confidence.
As the use of AI agents grows and they begin functioning autonomously, unique identities become essential. They help block unauthorized actions, meet compliance standards, and ensure a detailed audit trail is always available. This is especially crucial for businesses deploying AI agents in production settings, where maintaining transparency and control is absolutely essential.

