How MCP Secures Human-to-Agent Delegation
Sep 29, 2025
5
Matt (Co-Founder and CEO)
How MCP Secures Human-to-Agent Delegation
Enterprise AI agents need more than conversational abilities - they must act securely on behalf of users. The Model Context Protocol (MCP) ensures AI agents can access tools, data, and APIs within enterprises while maintaining strict identity and authorization controls. By replacing static credentials with user-specific, time-limited permissions, MCP minimizes security risks like over-permissioning and token misuse.
With features like scoped tokens, audit trails, and human-in-the-loop (HITL) workflows for high-risk actions, MCP allows businesses to automate workflows without compromising compliance or security. Platforms like Prefactor enhance MCP by offering centralized policy management, real-time monitoring, and integration with enterprise identity providers.
Key Takeaways:
Scoped Permissions: MCP ties agent actions to specific user identities, enforcing least-privilege access.
Audit Trails: Tracks every action for compliance and investigation purposes.
Human Oversight: HITL workflows require explicit approval for sensitive tasks.
Enhanced Security: Prefactor adds features like fail-closed policies and kill switches.
MCP and Prefactor make it possible to deploy AI agents securely, even in regulated industries like finance and healthcare. By combining identity-based delegation with robust governance tools, enterprises can automate critical tasks while maintaining control and transparency.
AWS re:Inforce 2025 - The right way to secure AI agents with code examples (IAM441)

Prerequisites for Implementing MCP with Prefactor

To successfully implement MCP (Managed Control Plane) with Prefactor, you'll need three key components: a Prefactor account, an MCP-compatible agent framework, and an OAuth 2.0 authentication system. These elements tackle common issues like over-permissioning, lack of visibility, and token misuse. Together, they ensure your AI agents operate under the same strict security standards as your human workforce by tying every action to a verified identity, enforcing least-privilege access, and maintaining detailed audit trails to meet regulatory demands.
AI Agent Framework Compatibility
Prefactor works seamlessly with MCP-compatible frameworks like LangChain and CrewAI, which support MCP clients for connecting to enterprise tools. To integrate these frameworks, register your agents as managed entities within Prefactor’s control plane. Each agent is assigned a unique identity, avoiding the common pitfall of shared service accounts, and receives short-lived OAuth 2.0 tokens scoped to specific tasks. For instance, a LangChain agent analyzing sales data might receive a token with "read:analytics" access valid for just 15 minutes. Audience validation ensures the token works exclusively with Prefactor’s MCP server.
This approach prevents token reuse and reduces the risk of a "confused deputy" attack. Prefactor also sanitizes inputs and runs MCP servers in sandboxed containers, minimizing the impact of any security breach. Additionally, it integrates with existing OAuth/OIDC systems like Auth0, Okta, Firebase, and Clerk, enabling agents to securely and programmatically access APIs and applications, much like human users. To ensure smooth operation, your frameworks must consistently represent user identity and session context, preserving this information across authorization and logging layers.
Authentication and Governance Requirements
Binding every action to a verified identity is non-negotiable for secure MCP implementation. This requires issuing OAuth 2.0 tokens with minimal scopes for each agent task, avoiding cascading permissions to downstream services. Prefactor enforces this by using mutual TLS (mTLS) for transport security and API token validation, ensuring every action is tied to a user identity. Tokens also include audience claims to restrict their usage. For non-human authentication, adopting OAuth 2.1 with PKCE is recommended by identity providers for added security.
Beyond authentication, you’ll need an enterprise identity provider (IdP) that supports OAuth 2.0/OIDC, a policy engine for granular authorization (like RBAC, ABAC, or CBAC), and a logging pipeline to feed MCP interactions into your SIEM system. Prefactor enhances these capabilities with human-in-the-loop (HITL) workflows for high-risk actions, such as wire transfers, production deployments, or bulk deletions. These workflows require explicit human approval before execution. For industries governed by regulations like SOX, HIPAA, or PCI, Prefactor’s SOC 2 compliance and detailed logging help meet audit requirements by tracking which agent initiated a transaction, under whose authority, and whether proper approvals were obtained.
How to Implement MCP for Secure Human-to-Agent Delegation
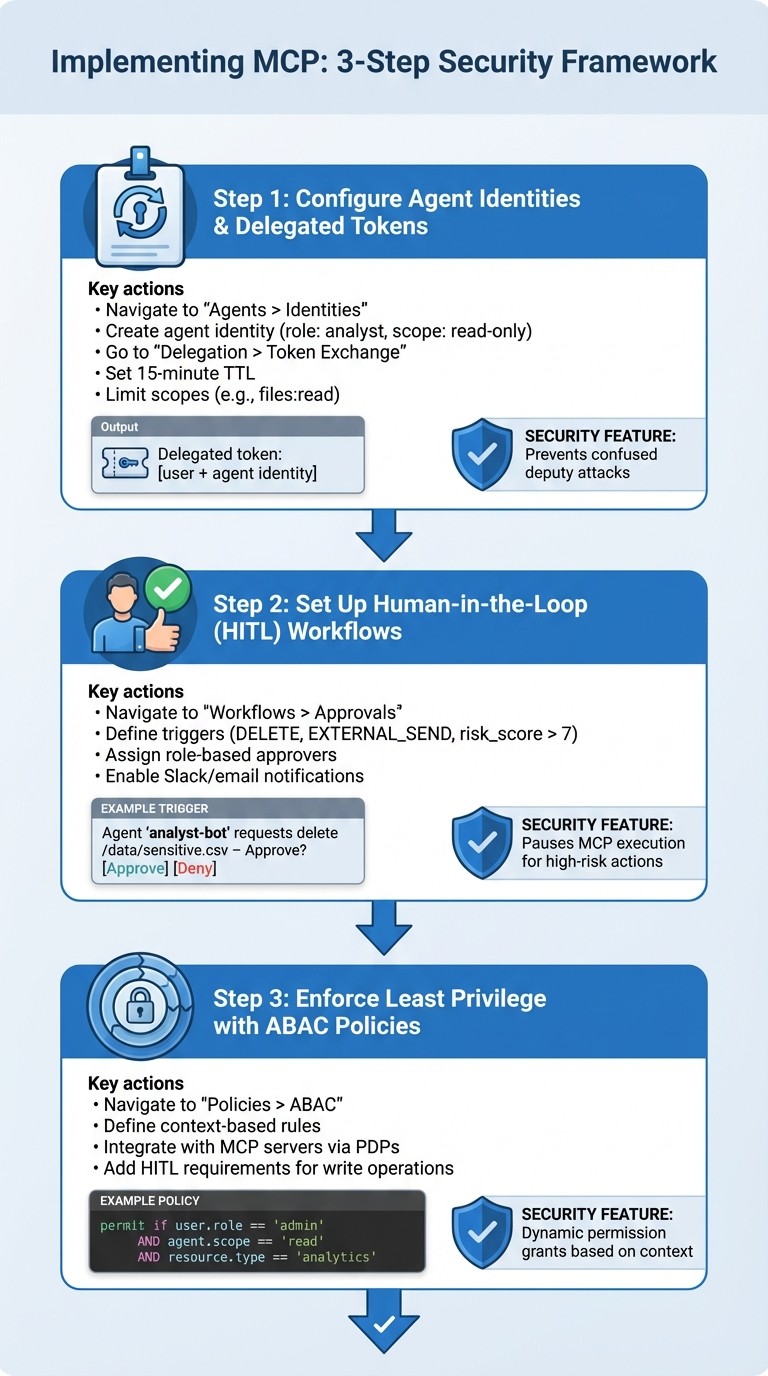
{MCP Implementation Steps for Secure AI Agent Delegation}
Configuring Agent Identities and Delegated Tokens
To set up secure human-to-agent delegation, start by using the OAuth 2.0 token exchange (RFC 8693) through Prefactor's dashboard. This process converts a user token into a delegated, scoped token, ensuring every agent action is directly tied to its authorizing human. Begin by navigating to "Agents > Identities" and creating a new agent identity with specific attributes like role: analyst and scope: read-only. Next, go to "Delegation > Token Exchange" to connect your OAuth provider (such as Auth0 or Okta) and configure token policies. Set a 15-minute time-to-live (TTL) and limit scopes to essentials like files:read, ensuring tokens are both minimal and audience-restricted.
To verify the setup, use the /token-exchange API endpoint with a user token as input. Prefactor will generate a delegated token embedding both the user and agent identities (e.g., agent_id and user_delegator). This creates a clear audit trail, linking every action back to the initiating human. By enforcing per-client consent and validating the audience before exchanging tokens, this approach prevents confused deputy attacks. Prefactor's policy engine strengthens security with Attribute-Based Access Control (ABAC) checks.
Once tokens are securely delegated, you can move on to configuring workflows that require human oversight for elevated actions.
Setting Up Human-in-the-Loop Approval Workflows
To manage high-risk actions, configure human-in-the-loop (HITL) policies in Prefactor. Go to "Workflows > Approvals" and define triggers for sensitive operations, such as action: delete, EXTERNAL_SEND, or conditions like risk_score > 7. Assign approvers based on roles (e.g., managers or on-call engineers) and enable notifications through email or Slack. These notifications should include full details, such as the tool name, parameters, and context of the action. For example, if an agent requests a destructive operation, Prefactor will pause the Managed Control Plane (MCP) execution and route the request to the /approval/pending endpoint. A Slack notification might look like this:
"Agent 'analyst-bot' requests delete /data/sensitive.csv – Approve?"
Here’s an example of a HITL policy configuration in JSON:
This workflow ensures that irreversible actions - like wire transfers, production deployments, or bulk deletions - are secured with human oversight. Every approval decision is logged for compliance and forensic analysis.
For added security, pair HITL workflows with ABAC policies to enforce least privilege access.
Enforcing Least Privilege with Granular Authorization
To ensure agents operate with the least privilege necessary, define ABAC policies in "Policies > ABAC". These policies dynamically grant permissions based on context. For instance:
Prefactor integrates these policies with MCP servers using policy decision points (PDPs), ensuring that every tool invocation complies with your defined rules. To address high-risk write operations, you can create additional policies requiring HITL approval. For example:
Monitoring and Maintaining MCP Security
Enabling Audit Trails and Real-Time Monitoring
Prefactor dashboards log every interaction within the MCP, providing a comprehensive audit trail that links each action to the responsible user. To access these logs, go to "Monitoring > Audit Trails". Here, you’ll find detailed records of tool usage, including invoked parameters, outcomes, and relevant business context like user identities, delegated permissions, and agent behaviors. These insights help identify issues such as over-permissioning or unauthorized tool usage.
For industries under strict regulations, like finance or healthcare, compliance alerts can be configured in "Alerts > Compliance". These alerts flag high-risk activities, such as repeated failed tool selections, excessive data access, or improper token use. For instance, if an agent tries to access production data without proper authorization, Prefactor immediately generates an alert. Additionally, you can integrate these audit trails with your SIEM system for a unified view of security events across your infrastructure. This real-time monitoring works hand-in-hand with preventative measures to address potential threats as they arise.
Configuring Kill Switches and Emergency Controls
Emergency controls, accessible through "Agent Controls > Kill Switches", allow for swift responses to security incidents. You can set up triggers for specific behaviors, like prompt injection attempts or confused deputy exploits, that automatically terminate sessions or revoke privileges. For example, a kill switch can block all delete operations on production data unless explicitly approved by a human, stopping unauthorized actions before they escalate.
Prefactor employs a "fail closed" policy, meaning operations cease if MCP services encounter issues, avoiding insecure defaults. This zero-trust approach ensures that every tool invocation is validated against permissions in real time. Features like one-click session invalidation provide immediate responses to threats. These controls also integrate seamlessly with human-in-the-loop approval workflows, ensuring that sensitive actions always require explicit consent. Pair these measures with regular security audits and performance evaluations for a robust defense.
Best Practices for Ongoing Security
Use Prefactor to conduct quarterly audits, identifying over-permissioning and token anomalies. Automated scans highlight violations of least privilege principles, allowing you to adjust permissions as needed. Incorporate MCP into your regular threat modeling and penetration testing routines. Simulating scenarios like confused deputy attacks or prompt injection attempts can help validate your defenses.
Keep an eye on key metrics - such as action volume, permission usage, and anomaly rates - to detect potential threats. For example, a sudden 20% increase in tool calls or unusual data access patterns could signal an issue. Prefactor’s real-time dashboards make tracking these metrics easy. One financial institution reduced its incident response time by 80% by leveraging continuous session validation. For added protection, run MCP servers in sandboxed environments with restricted privileges to minimize potential damage in case of a breach. Security professionals stress that consistent monitoring, human oversight for high-risk actions, and eliminating standing privileges are critical to overcoming the challenges that lead to the 95% failure rate in agentic AI projects.
Conclusion
Key Benefits of MCP
MCP turns AI agents from potential risks into secure, enterprise-ready tools by using strict token scoping, approvals involving human oversight, and enforcing the principle of least privilege. When paired with Prefactor, organizations gain the real-time visibility and compliance controls they need to address accountability challenges in AI-driven projects.
This setup offers practical operational advantages. Context isolation ensures data from one agent session doesn’t spill over into another, while fail-closed policies stop unauthorized actions before they escalate. Audit trails tie every agent action to the responsible user, adding transparency. Prefactor’s enterprise-level governance enhances scalability by offering agent-specific audit trails, seamless SIEM integration, and CI/CD-driven authorization workflows that are versioned and reviewable, much like other infrastructure. These safeguards make it possible to deploy autonomous agents safely, even in heavily regulated industries.
Next Steps
To take advantage of these benefits, follow these practical steps:
Set up a Prefactor account and confirm compatibility with your AI agent framework. Configure agent identities using short-lived tokens with minimal access, ensuring read-only permissions where applicable. For high-risk actions, such as modifying data or making production changes, enable human-in-the-loop workflows to maintain oversight. These measures are critical for reducing security vulnerabilities.
Integrate Prefactor’s monitoring tools with your current SIEM system to track essential metrics like action volume, permission usage, and anomaly rates that might indicate threats. Configure kill switches to respond to issues like prompt injection attempts, and use sandboxing to run MCP servers with restricted privileges.
Conduct quarterly audits to review security measures, maintain fail-closed policies, and remove standing privileges. These steps will help you build a scalable, secure defense tailored to your growing AI deployment needs.
FAQs
How does MCP ensure secure access control for AI agents in enterprises?
MCP assists enterprises in safeguarding their AI agents by implementing human-delegated access control within a strong and scalable authentication system. It works effortlessly with established identity frameworks like OAuth and OIDC, ensuring that agent identities remain both independent and trustworthy.
The protocol includes multi-factor authentication and offers comprehensive insight into agent activities through detailed audit logs. These capabilities help organizations mitigate risks, adhere to compliance requirements, and maintain control over their AI operations.
How does Prefactor ensure secure and effective AI agent permissions?
Prefactor secures AI agent permissions through the Model Context Protocol (MCP), which offers strong authentication and authorization measures. By supporting human-delegated access and dynamic agent registration, it easily connects with existing identity systems for a smooth integration process.
With features like real-time visibility, policy enforcement, and detailed audit trails, Prefactor equips enterprises to securely manage AI agent interactions while ensuring compliance, even in large-scale operations.
Why is human oversight essential for high-risk AI agent decisions?
Human involvement is crucial when AI systems make high-stakes decisions. It ensures accountability, precision, and safety by placing people at the center of critical processes. By doing so, organizations can minimize errors, avoid unintended outcomes, and maintain control over operations that require careful oversight.
This becomes especially essential in situations where AI decisions carry serious legal, financial, or ethical consequences. Human-in-the-loop systems act as a safety net, striking a balance between the speed and efficiency of AI and the thoughtful judgment and compliance that only humans can provide.

