Securing AI Agents with Role-Based Delegation
Oct 3, 2025
5
Matt (Co-Founder and CEO)
Securing AI Agents with Role-Based Delegation
AI agents are now performing tasks that involve sensitive data and critical systems, making security a top priority. Role-based delegation ensures these agents operate within strict, temporary permissions, maintaining control and accountability. Here's what you need to know:
What It Is: Role-based delegation assigns specific, limited roles to AI agents, defining what they can do, who authorized them, and under what conditions.
Why It’s Needed: AI agents don’t use traditional authentication like humans. They need tailored security measures to prevent risks like privilege misuse or unauthorized actions.
Key Practices:
Use least privilege principles to limit access.
Implement audit trails for full traceability.
Enforce strict authentication and authorization rules.
Separate tasks and environments to reduce risks.
These steps help businesses securely deploy AI agents while meeting compliance standards like HIPAA and SOX. The goal is to ensure every action by an AI agent is traceable, limited in scope, and aligned with organizational policies.
AWS re:Invent 2025 - Securing AI Agents: The Future of Identity & Access Control (SEC328)
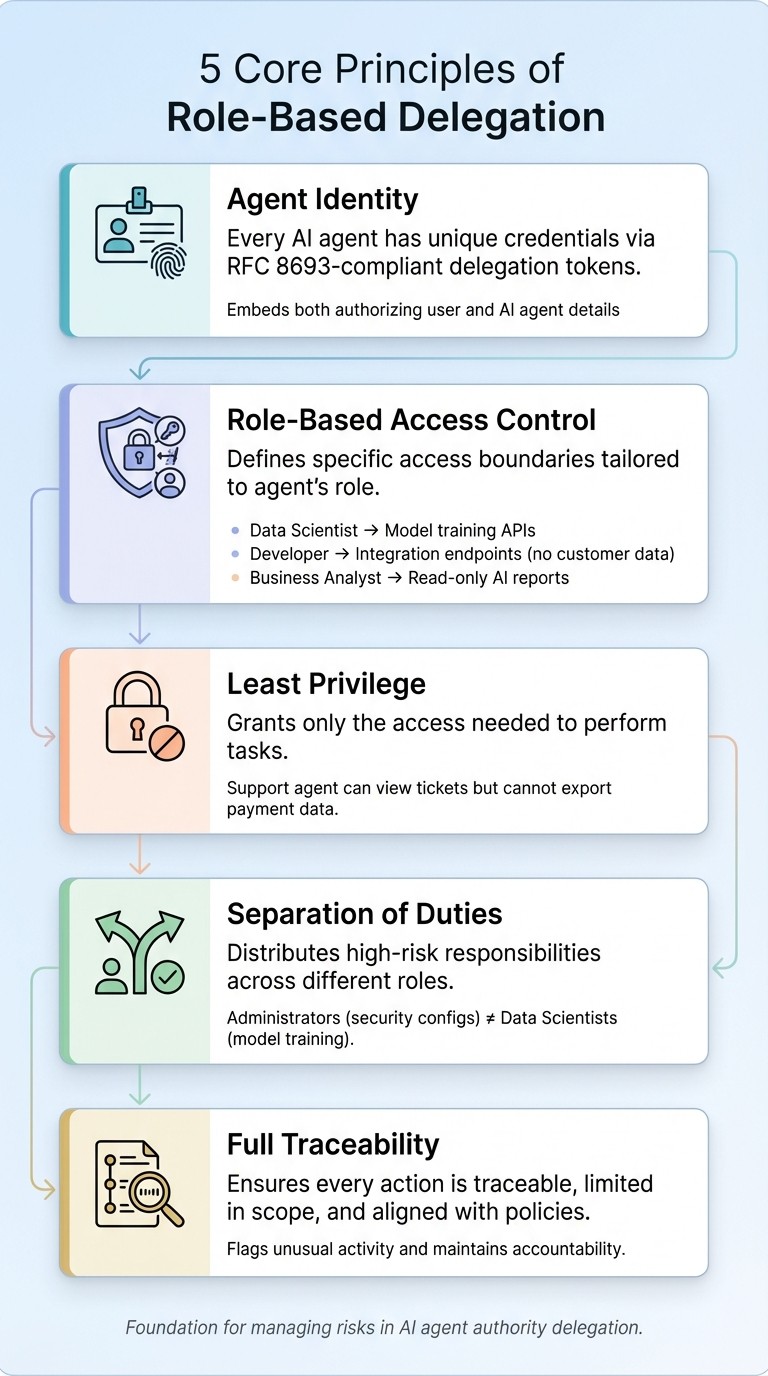
Core Principles of Role-Based Delegation
{5 Core Principles of Role-Based Delegation for AI Agents}
Key Concepts in Role-Based Delegation
When it comes to securely delegating tasks to AI agents, five principles form the backbone of the process. The first is agent identity, which ensures every AI agent has unique credentials. These credentials often come in the form of RFC 8693-compliant delegation tokens, embedding details about both the authorizing user and the AI agent itself.
Next is Role-Based Access Control (RBAC), which defines specific access boundaries tailored to an agent’s role and operational context. For example, a Data Scientist role might have permissions to access model training APIs, while a Developer role could interact with integration endpoints but would not have access to raw customer data . This alignment between permissions, technical needs, and security policies ensures agents operate within clearly defined limits.
The principle of least privilege is another cornerstone, granting agents only the access they need to perform their tasks. For instance, a Business Analyst agent might only have read-only access to AI-generated reports, while a support agent could view customer tickets but would not be allowed to export sensitive payment data . Separation of duties further enhances security by distributing high-risk responsibilities across different roles - for instance, administrators handling security configurations are kept distinct from data scientists focused on model training.
Together, these principles create a foundation for understanding and managing the risks that come with delegating authority to AI agents.
Security Risks in Delegating Authority to AI Agents
While delegation is essential, it introduces certain vulnerabilities that need to be addressed. One of these is confused deputy attacks, where an agent misuses its delegation token to access resources beyond the original user’s intent. This happens when a gap exists between the technical permissions granted and the user’s actual intentions. Another risk is prompt injection, where malicious instructions are embedded in user inputs or external data, potentially bypassing security measures.
A third concern involves overly broad tool scopes. For example, a DevOps agent with unrestricted deployment permissions could inadvertently - or intentionally - make changes to production systems it was never meant to control . In systems with multiple agents, these risks can escalate. If an orchestrator agent is compromised, it could trigger unauthorized actions across all connected worker agents. Implementing RBAC with granular permissions and detailed audit trails can help mitigate these risks by flagging unusual activity .
Structuring Tools and Resources for Delegation
To counter these risks, it’s crucial to organize tools and resources thoughtfully. One effective strategy is grouping tools into role-specific bundles. For instance, customer support tools could include ticket viewing and basic refund processing, while infrastructure tools might handle tasks like service restarts or deployment rollbacks. This setup creates clear security boundaries.
Another layer of protection comes from separating environments. Development agents should operate in sandboxed settings with synthetic data, while production agents work under stricter controls with access to real customer information. This separation minimizes the impact of errors during testing - if a development agent malfunctions, live systems remain unaffected. Delegation tokens within these environments should include contextual constraints, such as allowed regions, time frames, or resource types .
In multi-agent systems, the way tools are assigned plays a critical role. Assign worker agents to handle execution tasks, while manager agents focus on planning and coordination without direct access to tools. This reduces the risk of orchestration prompts leading to unintended tool usage. Additionally, policy engines like Open Policy Agent (OPA) can dynamically evaluate whether a specific agent-tool combination is allowed, taking into account user and agent identities, the task context, and organizational rules. This structured approach ensures that role-based delegation remains secure throughout the lifecycle of AI agents.
Designing Role Models and Delegation Flows
Creating Task-Specific and Environment-Specific Roles
The foundation of secure AI agent management lies in designing roles tailored to specific tasks and environments. For instance, a Claims Agent role should strictly handle querying claim databases, validating documents, and updating statuses - nothing more. This approach embodies the principle of least privilege, where roles are equipped with only the essential tools and access needed for their function, while everything else is restricted. When defining these roles, it’s critical to outline specifics like permitted APIs, data domains, CRUD operations, rate limits, and any required approvals.
Separating roles by environment is equally important. Development roles usually have broader access to synthetic data and mock APIs for testing purposes. In contrast, production roles enforce stricter controls, such as read-only access or rate limits on live systems. By embedding environment attributes directly into delegation tokens, policies can automatically enforce these boundaries while providing an auditable record of actions.
Defining Delegation Patterns
Once roles are established for tasks and environments, the next step is to define how authority flows within the system. Delegation patterns ensure clear and secure transitions of authority.
Human-to-agent delegation: This involves token exchanges (aligned with RFC 8693), where scoped authority is granted by embedding both the user’s and the agent’s identities into a single token.
Agent-to-agent delegation: Here, tasks are handed off between agents. A primary agent delegates subtasks to specialists, progressively narrowing permissions to prevent misuse or privilege escalation.
Agent-to-tool delegation: This pattern binds agents to specific APIs using signed credentials. Tools then validate the agent’s identity and enforce limits before executing any actions.
Okta highlights the importance of scope attenuation in delegation chains, ensuring each handoff reduces permissions to minimize risks from compromised agents. For complex workflows, implementing a supervisor/worker model can help. In this setup, a supervisor breaks down tasks into smaller components, and workers perform these tasks with narrowly defined roles.
Integrating Role Models into Development Workflows
With roles and delegation patterns clearly defined, embedding these models into development workflows ensures security becomes a built-in part of the software lifecycle. Treating roles as code shifts security from being a runtime concern to a fundamental development practice. Role definitions - including permissions, tools, and environmental constraints - should be version-controlled. Automated checks during continuous integration (CI) can validate these policies, comparing any changes against least-privilege baselines. Open Policy Agent (OPA) unit tests can further ensure that high-risk actions still require proper approvals.
WorkOS recommends integrating automated permission scans into CI/CD pipelines to detect and prevent over-privileging before deployment. Additionally, scoped credentials and delegation tokens should be automatically generated and versioned during these pipelines, ensuring policies remain both testable and reviewable. This approach solidifies secure and auditable AI management as a core part of the development process.
Authentication and Authorization for AI Agents
Establishing Strong Agent Authentication
AI agents need their own unique identities, separate from human users. Traditional methods like MFA or CAPTCHAs can interfere with automation, so it's better to link agent identities to enterprise identity providers such as Okta or Azure AD. This can be achieved using technologies like mTLS or token-based approaches such as OAuth 2.0 and JWTs.
With mTLS, both the agent and the service authenticate each other using client certificates issued by a trusted certificate authority. This ensures mutual verification, reducing the risk of impersonation. For token-based access, agents are issued short-lived JWTs after an initial authentication process, with scopes tailored to their specific tasks. To enhance security, tokens should be rotated using refresh mechanisms, their signatures validated at API gateways, and their status checked for revocation through token introspection endpoints. This helps prevent replay attacks.
Integrating agents with existing OAuth or OIDC-based identity solutions simplifies management. By leveraging federated identity providers, agents can assume predefined roles, reducing the need to maintain separate credentials.
Implementing Least Privilege in Authorization
Once authentication is secured, authorization ensures agents operate with only the access they truly need.
The principle of least privilege should guide permissions. This means granting agents only the minimum access required for their tasks. For instance, a fraud detection agent might only need read-only access to transaction databases. Use task-specific roles with explicit allow rules and adopt a deny-by-default approach to further tighten security.
A 2024 Forrester report found that companies using Role-Based Access Control (RBAC) for AI agents reduced unauthorized data access incidents by 40%. Limiting privileges also significantly reduced the potential impact of breaches. Tools like AWS IAM or Okta can define fine-grained scopes for agents. For example, a customer support AI could have read-only access to inquiry tickets and CRM data but be denied write permissions or access to sensitive HR systems. During development, simulate unauthorized access scenarios to ensure deny-by-default policies are effectively blocking restricted actions.
Combining RBAC with Contextual Attributes
Static roles alone may not be enough in dynamic environments. Adding contextual factors to permissions can refine access control even further.
By combining RBAC with Attribute-Based Access Control (ABAC), you can integrate dynamic elements like time, location, or data sensitivity into authorization decisions. For example, an analytics agent might only access production data during specific time windows and from trusted corporate IP addresses.
Tools like Open Policy Agent (OPA) can evaluate these contextual attributes in real time, enabling adaptive authorization. In financial systems, IP-restricted roles have been shown to prevent 30% of potential data exfiltration attempts during audits by limiting access to approved network locations. This hybrid approach merges the structured framework of RBAC with the adaptability of ABAC, allowing for security policies that adjust seamlessly to changing conditions without manual updates.
Monitoring, Auditability, and Governance for AI Agents
Establishing End-to-End Traceability
Traceability involves tracking every step an AI agent takes, starting from a human's initial request, through the agent's decision-making process, and onto the systems it interacts with. Without full visibility, agents can unintentionally go beyond their intended scope, especially in scenarios involving multiple agents working together. To maintain control, use RFC 8693-compliant delegation tokens. These tokens embed details about both the initiating human and the AI agent, ensuring context is preserved throughout the process. Pair this with Open Policy Agent (OPA) to enforce consistent authorization rules. Every system interaction, such as tool usage and API calls, should include a unique correlation ID. This ID enables structured logging with key fields like request_id, user_id, agent_id, role, scope, resource, action, and timestamp. Such detailed logging makes it easier to conduct investigations and audits when needed.
Building Audit Trails
An effective audit trail captures critical information, including the identities of users and agents, actions taken, timestamps, roles, and relevant context. To ensure these records are trustworthy, use structured logging with signed credentials at every delegation point. Store these logs in tamper-evident systems to create immutable and verifiable records. Regularly reviewing these logs should be part of your access reviews and incident response plans. This proactive approach helps identify unauthorized actions or privilege escalations before they become bigger issues. Verifiable audit trails are the backbone of centralized governance for AI agents, ensuring accountability at every level.
Using Agent Control Planes for Governance
Centralized agent control planes build upon traceability and audit trails to streamline governance and compliance. Without a centralized approach, organizations risk the rise of "shadow agents" - agents that bypass logging, approval workflows, and compliance measures. Control planes act as a unified platform for managing policies, monitoring activity in real time, and generating compliance reports. For instance, Prefactor provides features like centralized audit trails, real-time dashboards, and compliance controls tailored for production environments. These platforms track active agents, monitor tool usage, and log high-risk actions. They often include emergency kill switches and just-in-time access controls, which limit permissions to only when they’re needed. This centralized oversight complements the secure delegation framework, enabling organizations to define access rules once and scale them efficiently. For U.S. companies bound by regulations like SOC 2, HIPAA, or PCI, treating AI agents as privileged technical users - subject to the same rigorous standards as human accounts - is becoming a best practice.
Operational Best Practices and Compliance
Operational Controls for Secure Agent Management
Turning security principles into actionable steps is key for managing AI agents securely on a daily basis. Treat changes to agent permissions like updates to critical infrastructure - implement change management processes to ensure every adjustment is logged, reviewed, and approved. Tools like AWS IAM or Okta can enforce version-controlled policies, reducing the risk of unauthorized modifications. For example, quarterly access reviews have been shown to cut unauthorized incidents by 40%. Limiting fraud detection agents to only access transaction data, instead of entire customer databases, is another simple way to reduce risk exposure.
If an agent is compromised, immediate action is critical. Revoke delegation tokens (following RFC 8693 guidelines) and isolate affected systems to contain the issue. Safety measures like dead letter queues (DLQs), timeouts, and human-in-the-loop controls for high-risk tasks - such as legal approvals or budget sign-offs - add extra layers of protection. A structured rollout plan could start with defining contracts, schemas, and quotas over a couple of weeks, followed by proof-of-concept testing with close supervision, and finally scaling under governance board oversight to manage roles, approvals, and capacity planning. These steps integrate seamlessly with broader governance strategies.
Regulatory Alignment for U.S. Enterprises
For U.S. companies, regulations like HIPAA and the Gramm-Leach-Bliley Act (GLBA) demand that AI agents meet the same rigorous standards as human users with privileged access. HIPAA, for instance, requires auditable logs of PHI access to be kept for at least six years, alongside U.S.-based data processing. Similarly, GLBA mandates five to seven years of access log retention, annual compliance audits, and regular risk assessments for AI systems handling sensitive data.
Healthcare AI systems working with medical records should be restricted to specific PHI datasets using granular permissions. Financial AI systems, on the other hand, should enforce encryption and geographic restrictions through cloud IAM tools. Detailed logging - capturing fields like agent_id, role, resource, action, and timestamp - provides clear audit trails, making compliance investigations and incident forensics more efficient.
With these compliance measures in place, the focus shifts to scaling AI deployments securely.
Scaling Secure AI Deployments with Prefactor

Prefactor simplifies secure scaling by embedding policy-as-code into CI/CD pipelines, addressing governance gaps that often derail AI projects. Organizations can define role-based access control (RBAC) rules programmatically, automating enforcement during deployments and reducing manual workloads. Prefactor’s SOC 2 compliance, real-time dashboards, and just-in-the-loop controls make it easier to meet U.S. regulatory requirements while scaling AI operations.
The platform tracks active agents, monitors tool usage, and flags risky actions. Emergency kill switches and just-in-time access controls ensure permissions are only granted when absolutely necessary. By treating AI agents as independent identities with secure, autonomous authentication - rather than relying on traditional methods like MFA - Prefactor helps enterprises move from testing to full-scale deployment while maintaining the accountability and control regulators expect.
Conclusion and Key Takeaways
Securing AI agents through role-based delegation is a critical step in moving from experimental projects to secure, production-ready deployments. Consider this: 95% of agentic AI projects fail due to accountability gaps, and breaches involving misused credentials cost organizations an average of $4.6 million. The solution lies in treating AI agents as first-class identities, ensuring they have only the scoped, auditable access they need - no more, no less.
To address the risks outlined earlier, adopt a least-privilege authorization model. This approach limits each AI agent's access to only the tools and data necessary for its tasks. Use RFC 8693 tokens to enable clear multi-hop attribution, ensuring every action is traceable. Without robust traceability and audit trails, organizations risk being unprepared when incidents arise or regulators demand accountability.
But security isn't just about technical controls - it’s about discipline. Permission changes should be treated like updates to critical infrastructure: logged, reviewed, and approved through strict workflows. Safety measures such as kill switches, timeouts, and human-in-the-loop approvals for sensitive tasks add another layer of protection. These practices align with U.S. regulatory standards, ensuring compliance and robust security.
Centralized tools can simplify these processes. For example, Prefactor integrates policy-as-code into CI/CD pipelines, offers real-time dashboards, and enforces SOC 2 compliance with just-in-time access controls. By addressing governance gaps, tools like this empower enterprises to scale AI agents securely and confidently.
With the right delegation framework and governance tools in place, AI agents can transition from being experimental risks to accountable, secure contributors to business success. Role-based delegation isn’t just a best practice - it’s essential for building trust and value in AI deployments.
FAQs
How does role-based delegation enhance the security of AI agents?
Role-based delegation enhances the security of AI agents by assigning them specific access permissions tied to clearly defined roles. This means each agent is limited to performing tasks and accessing data strictly within its designated responsibilities, reducing the chances of misuse or unauthorized actions.
This approach also introduces scalable and trackable access controls, making it easier for organizations to monitor agent behavior and hold them accountable. By providing a structured way to manage permissions, role-based delegation ensures AI agents function securely and adhere to company policies.
What are the main risks of giving AI agents decision-making authority?
Delegating decision-making authority to AI agents introduces several risks that need careful consideration. One major concern is the loss of control over the actions of these agents, which can sometimes result in unintended or even harmful outcomes. There's also the issue of security vulnerabilities - AI systems might expose sensitive data or inadvertently allow unauthorized access.
Another challenge lies in maintaining accountability. Tracing decisions back to specific actions or inputs can be tricky, making it harder to ensure compliance and maintain transparency. Without sufficient oversight, these gaps can lead to operational and regulatory issues. To address these concerns, implementing strong safeguards is not just advisable - it's essential.
What steps can organizations take to ensure compliance when using AI agents?
To maintain compliance when deploying AI agents, organizations need to establish role-based delegation alongside strong practices for authentication, authorization, and monitoring. These steps are essential for setting clear security boundaries and ensuring compliance for AI operations.
On top of that, using tools like Prefactor can make a big difference. Prefactor offers features such as real-time visibility, audit trails, and policy enforcement, which allow businesses to scale their AI agents securely. These tools also help organizations retain control over operations while meeting all necessary compliance standards.

